Facial Recognition for Access Control and Authentication
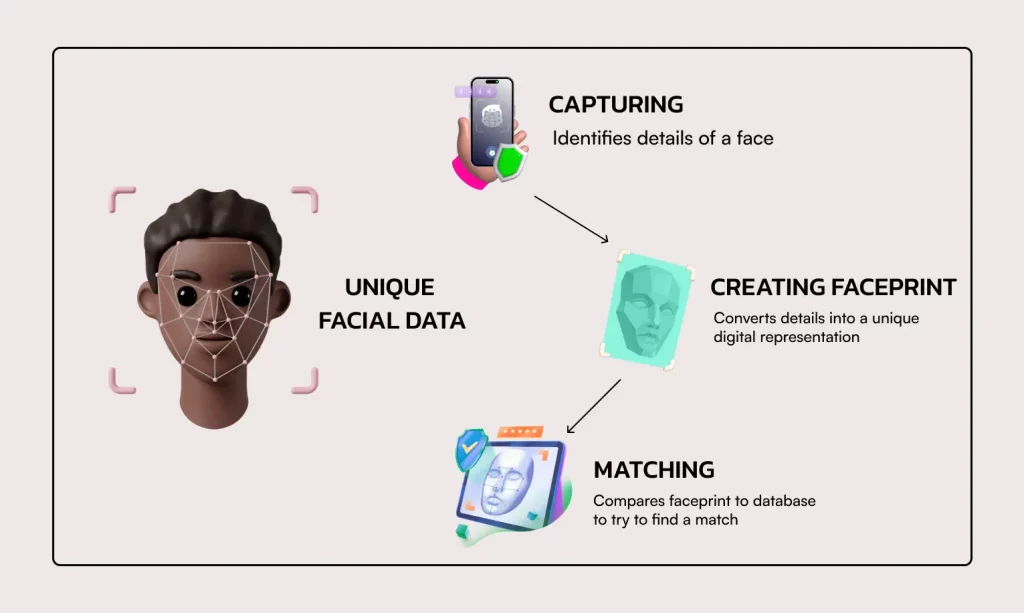
Using facial traits, this technology can identify or confirm a person's identity. To determine a match, it maps face traits from a photo or video using biometric software and compares the results with a database. Facial recognition has become a powerful tool for security because of its increased accuracy and dependability.
Facial recognition access control procedure
Using facial recognition for access control relies on a number of interrelated processes, each supported by sophisticated machine-learning techniques and scientific algorithms.
Step 1: Obtaining the image
The first step in the facial recognition process is image acquisition.
The system's high-definition cameras record a picture or video frame containing a face, which is then saved in an access control database.
In order to achieve the best results in all lighting circumstances, contemporary facial recognition systems use infrared cameras since the quality of the image collected is crucial.
Step 2: Identification of faces
A face must be able to be recognized by the system when it approaches an access point after it has been added to the access control database. We name this phase face detection. It entails recognizing faces in people.
To effectively distinguish faces, advanced machine learning algorithms like Convolutional Neural Networks (CNN) take into consideration variables like angle and distance.
Step 3: Preprocessing
Preprocessing, the third stage, increases the precision of all ensuing facial recognition procedures.
Normalization, which aligns faces to a standard size and orientation, and illumination correction, which modifies lighting conditions to enhance image quality, are two of its components.
Step 4: Extracting features
Facial recognition relies heavily on feature extraction. It involves turning a detected face's distinctive characteristics—like the separation between eyes or the nose shape—into a numerical representation called a facial signature.
Step 5: Decision making and matching
The facial signature is compared to faces in the system database using Cosine or Euclidean distance similarity metrics in the matching and decision-making phase, which is the last stage.
If the face matches preprogrammed site authorizations, access is then either allowed or prohibited.
With each new access attempt, access control systems that use Adaptive and Self-Evolving Systems (ASES) technology can learn. For long-term accuracy, facial recognition systems can gradually enhance their algorithms through continuous learning.
Uses of access control systems with facial recognition
Corporate environments
Facial recognition access control systems have been implemented by numerous corporate offices in order to secure their facilities. These systems make sure that only people with permission can enter private spaces like executive offices and server rooms. In addition to safeguarding priceless goods, this improves workplace security generally.
Schools and institutions
A face access control system can help schools and universities improve campus security by limiting building entry to approved visitors, employees, and students. Students and employees' general safety can be enhanced by this technology, which can also help stop unwanted access.
Healthcare industries
To safeguard patient data and medical supplies, healthcare facilities—including clinics and hospitals—must enforce stringent access control. In addition to providing authorized people with rapid and simple access, these technologies efficiently safeguard these environments.
Residential buildings
People of residential complexes can enter their houses safely and conveniently with the help of facial recognition access control systems. In order to improve security for all residents, property managers can keep an eye on and regulate visitor access.
Hospitality and retail
Facial recognition technology can be used in retail and hospitality to restrict access to back-of-house spaces, allowing only authorized personnel to enter. This improves the security of sensitive data and priceless goods and helps deter theft.
Governmental and public infrastructure
Public spaces and government buildings can be used to protect sensitive sections and guarantee that only individuals with permission can enter. As a result, these vital infrastructures are safer and more secure overall.
Transportation centers
Transportation hubs such as rail stations and airports can considerably benefit from facial recognition access control systems. Only authorized staff can enter restricted areas with facial recognition systems, which can also improve security checks and expedite the boarding procedure. This enhances general safety and effectiveness, assisting in the efficient handling of the large number of passengers.
Possibilities of facial recognition access control in the future
Developments in AI and machine learning
Ongoing developments in artificial intelligence and machine learning are making facial recognition systems more accurate and efficient, increasing their dependability and effectiveness.
Prospects for wider uses
The range of possible uses for facial recognition technology is growing beyond conventional security applications, opening up new and developing industries.
Advancements in technology for facial recognition
Facial recognition systems are becoming increasingly advanced due to advancements in facial recognition technology, which have increased their accuracy, speed, and dependability.
Use Lystface face recognition software that uses advanced facial recognition technology to safeguard your data without any loss. Additionally, Lystface API is available for seamless integration with your existing system.



